Insight & Resources
Explore our latest research, insights, and customer success stories, helping you drive business change faster.
View all
Outside of your centralised control you can’t see whether these gadgets have outdated software or are infected by malware. You also can’t monitor how your employee is behaving or using your business’s tools. This increases the window for potential attacks which could have big repercussions for your organisation, its team and customers.

Tight browser security is essential to protect your business during your employee’s live web sessions. It ensures remote work security for teams and suppliers who need to access tools and information to do their job outside the office. Here, we set out the steps you can take to effectively integrate browser security.
Implementing tight security policies on unmanaged devices is the most essential step to protecting your organisation. This includes setting these rules and guidelines out clearly and putting disciplinary actions in place for anyone who breaches them. You should also review these policies regularly to make sure they’re up to date.
The specifics will be adapted to your particular organisation’s needs, but may cover:
Implementing multi-factor authentication (MFA) to access key accounts and tools under a Zero Trust policy
Restrictions over using devices in shared spaces or on public networks
Data protection guidelines for processing, sharing and storage

You may need to implement specific tools to equip employees and suppliers to follow these policies. They should also be reviewed regularly to make sure they’re operating effectively and maintaining your compliance standards.
Secure browsers offer businesses real-time, centralised control without limiting the flexibility remote workers need. They make it possible to set browser policies, monitor data transfers and block third-party trackers or potentially dangerous actions without disrupting the user experience.
Advanced endpoint security tools like Chrome Enterprise Premium give businesses even more security with:
Access to reports about user actions, app usage and data movements
Default protections such as site isolation, sandboxing and predictive phishing tools
The ability to create rules that restrict the use of unapproved tools including extensions, website or SaaS apps
Data loss prevention controls, including generating watermarks over sensitive data, restricting data download only to restricted devices and the automatic saving of downloaded data files for further investigation
The ability to set a minimum OS version, ensuring user’s personal devices have the most up-to-date software
This means even businesses with the tightest security compliance requirements can offer their workers more flexibility, without compromising on standards.
Making employees and third-party suppliers aware of the security risks of unmanaged devices will give you an effective first line of defense. Making the importance of simple changes clear, such as keeping software updated, setting strong passwords and making sure email spam filters are set will maintain security without overwhelming employees.

Putting helpful tools in place will also make it easier for colleagues to maintain high security standards. For example, password manager apps will ensure login details are regularly refreshed and less likely to forget or write them down. Sharing clear security tips and running regular user education sessions will keep best practices front of mind.
Putting multiple tools in place will ensure the security of unmanaged devices without hampering their performance. For example, you could implement:
VPNs require remote devices to dial in to access company networks and data. This allows businesses to have control and some visibility over user activity, although additional vulnerability management is required to maintain full protection
Endpoint Detection and Response (EDR) tools make it possible for businesses to continuously monitor user activities, detect threats and take action to contain them
Remote browser isolation technologies separate any users’ internet activities from the device via the cloud. This helps protects any data, devices and networks from malware and malicious activity
To ensure your browsers are always secure and compliant, it’s essential that your business’s configurations are regularly audited. Using tools such as Chrome DevTools Lighthouse or third-party services, these audits will identify any vulnerabilities and risks to your business data or security.
Any discrepancies between your company’s policies and the actual browser settings can then be addressed. This could include implementing any required updates, removing unauthorised extensions and fixing any accounts and permissions that are being incorrectly used. Running this process regularly will help you meet compliance rules.
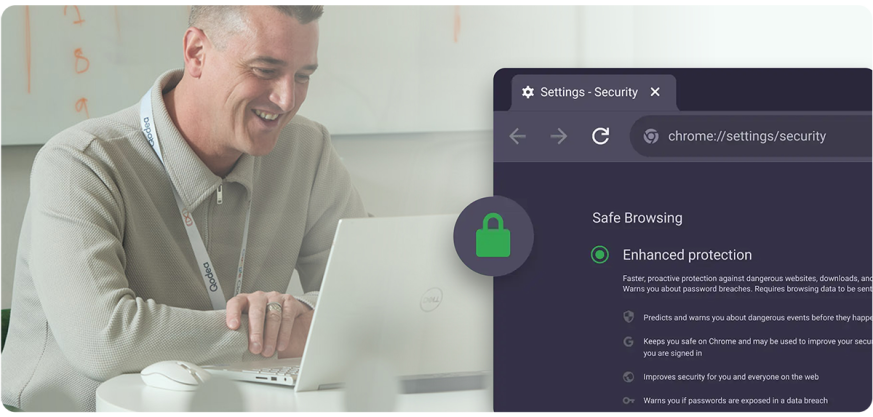
Using the right security policies and technologies to manage any unmanaged devices will mean you can both protect your business and give employees flexibility. Without restricting user experiences, it helps technical teams have visibility and control over personal laptops and phones.
With this, businesses can:
Reduce their potential attack surface and reduce the risk of data breaches or cybersecurity threats
Protect their business’s intellectual information and customers’ personal data, with the ability to monitor and control data sharing
Strengthen their cybersecurity infrastructure and ensure they maintain regulatory compliance
Prevent the need for system shutdowns or security-related disruptions due to breaches, maintaining productivity
Having these systems in place will also help protect employees and third-party suppliers from any disciplinary or legal actions from inadvertent or deliberate security breaches.
By following the guidance above, you can help your whole team do their job effectively without putting your business’s security at risk. This will ensure you meet your compliance obligations and keep both customers and employees safe.
To find out more about how secure browsers could benefit your business, download the Future of Enterprise Browsers report.
DownloadDiscover how tomorrow starts now
Get in touch